As of May 11, Colonial was returning portions of the critical artery for East Coast gasoline and refined fuel supply to service. While government officials and industry analysts did not anticipate widespread supply disruptions, the high-profile event caused filling station shortages in the Southeast and raised concerns about the prospect of future pipeline shutdowns at a time of rising cyberattacks.
|
U.S. Energy Secretary Jennifer Granholm on May 11 asked Americans to avoid hoarding gasoline and urged them to report price gouging. Source: Jennifer Granholm |
Renewed calls for federal pipeline cybersecurity standards
In the wake of the incident, Federal Energy Regulatory Commission Chairman Richard Glick reiterated his support for mandatory cybersecurity standards for pipeline operators. FERC approved minimum cybersecurity reliability standards for the electric power grid in 2008. Glick on May 11 said those standards do not mean the grid is secure, but they provide a "floor." He said he finds it "troubling" that there is not a similar regime for pipeline operators.
In a June 2018 op-ed, Glick and Chatterjee said the time had come for minimum pipeline standards, particularly in light of natural gas's growing role in U.S. electric power generation.
Shortly after Chatterjee and Glick expressed their views to Congress in June 2019, Moody's issued a report that found cybersecurity standards would bolster the creditworthiness of midstream companies and the electric power utilities they supply. On May 10, Moody's said the Colonial incident meant U.S. energy infrastructure assets will likely face heightened regulatory scrutiny.
Asked if he agreed with Glick, Mayorkas said the Biden administration is discussing measures at the executive level and in partnership with Congress to "raise the cyber hygiene across the country."
The Transportation Security Administration within DHS has responsibility for pipeline cybersecurity. Mayorkas noted that DHS and TSA share information and best practices with pipeline operators. TSA also dispatches personnel to pipeline facilities to assess them and make recommendations.
"There are different levels of strength and resilience across the critical infrastructure enterprise, and that is why we are so focused on making sure that the cyber hygiene across the entire enterprise is strengthened," he said. "And remember, in cybersecurity, one is only as strong as one's weakest link, and therefore we are indeed focused on identifying those weak links."
TSA's cybersecurity credentials under scrutiny again
Sen. Edward Markey, D-Mass., on May 8 called the TSA too understaffed and underprepared to ensure the safety of natural gas pipelines.
Markey referenced U.S. Government Accountability Office reports in recent years that identified weaknesses in TSA's pipeline cybersecurity program, including chronic understaffing and a lack of cybersecurity expertise. The TSA has closed seven of 10 GAO recommendations since they were issued in December 2018. Open recommendations include developing a strategic workforce plan; coordinating an external review of TSA's tool for ranking pipeline risk; and incorporating new threat, vulnerability and consequence data sources into the tool.
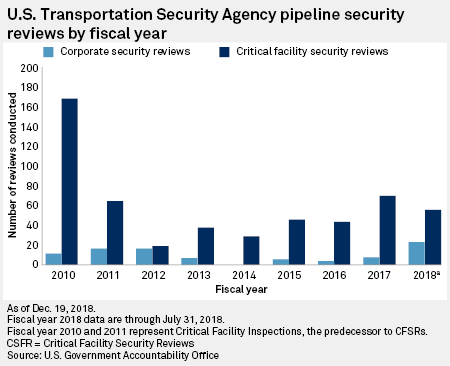
Asked about TSA's long-standing staffing problems, Mayorkas said the administration recently launched a series of cybersecurity "sprints," with the first focused on ransomware and the second aimed at recruiting and retaining top cybersecurity talent.
Rep. Emanuel Cleaver, D-Mo., sought to tackle TSA's shortfalls in 2019 by introducing legislation that addresses several GAO recommendations, including regularly updating industry guidelines, developing a personnel strategy and recruiting cybersecurity experts.
Glick and Chatterjee have advocated a different approach: transferring TSA's pipeline cybersecurity responsibilities to the U.S. Department of Energy. They also noted in the 2018 op-ed that TSA has the authority to impose minimum standards but chooses to rely on voluntary ones.
Some say regulations are not the answer
Cybersecurity professionals have warned that best practices are not ironclad and may not prevent another whole-system shutdown, though some feel similarly about regulation.
"Regulation is just one tool in the toolbox, and regulation inherently ... lags risk," Siemens Energy AG Vice President and Global Head of Industrial Cyber and Digital Security Leo Simonovich said in an interview. "It has its usefulness in creating some basic hygiene standards, and it's done quite a bit of good for the electric sector."
The American Petroleum Institute on May 11 said it was premature to craft regulations in direct response to the hack until the details of the incident are known. Rather, the trade group said it was more constructive to adopt more flexible policies down the line that allow companies to adapt to evolving threats. API also said the incident demonstrated that the U.S. needs more pipeline infrastructure to ensure redundancy in the system.
Top Republicans on infrastructure-focused committees shared that view in a May 11 news release. "Cyberattacks on our infrastructure network represent an ongoing, serious threat to our national security. However, it also highlights the continued need for projects that would expand our capacity for safely and efficiently moving goods and people," said Rep. Sam Graves, R-Mo., ranking member of the Transportation and Infrastructure Committee, and Rick Crawford, R-Ark., ranking member of the Railroads, Pipelines and Hazardous Materials Subcommittee.
Graves and Crawford said the canceled Atlantic Coast Pipeline LLC and disputed Mountain Valley Pipeline LLC projects "would have also created a significantly greater capability to respond to this cyberattack." Those projects would increase natural gas transportation capacity on the East Coast. The Colonial system carries gasoline and other refined liquid fuels from Texas to New Jersey.




