Introduction
Over the past several months, we have tracked the impact of the global pandemic on businesses, with emphasis on how IT has enabled businesses to adapt to radically changed realities. We have seen how the technologies of remote work made it possible for millions around the world to maintain the social distancing necessary to stem the spread of contagion while operating as normally as possible.
The scale of the shift and its implications were often far beyond what many organizations may have been prepared for. Securing this transformation has become a top priority for organizations, as revealed in recent 451 Research Voice of the Enterprise (VotE) survey data. But the need for change in security strategy that COVID-19 has revealed goes beyond immediate demands, and speaks to a growing awareness of the longer-term impact of IT transformation.
The 451 Take
Securing vastly expanded access means more than adapting to the realities of a global pandemic. In the long run, it will mean confronting the realities of the evolving nature of enterprise IT – not just millions of new remote endpoints, but also the proliferation of tens or hundreds of third-party IT services that substantially alter the nature of risk control for the business. Add to this the expected explosion in new types of endpoints and edge computing models, 5G and operational technologies, and the nature of enterprise security only a few years if not a few months hence begins to look very different.
In our VotE studies of the impact of coronavirus, we have seen that organizations expect recovery to last longer than initially anticipated, and many of the changes wrought to endure. For security, concerns about protecting the organization from the impact of adaptation to new workplace realities may only serve to make plain what has been implicit for years: Enterprise IT has expanded far beyond concepts of the traditional enterprise, and security needs to expand along with it.
Precipitating needed change
Adapting the enterprise to remote work at scale meant that hundreds or thousands of home networks became extensions of the business, but not always with the same level of risk assurance that organizations have from the on-premises network. It often meant embracing third-party resources such as digital workspace, teleconferencing and collaboration technologies delivered from the cloud, and directly accessible to users without having to go through the enterprise network.
These factors often introduce substantial security problems for the many businesses that rely on the deployment of security measures within the legacy enterprise environment. How do these organizations ensure their security when users can connect directly to third-party assets, cutting enterprise measures out of the picture (and often with better performance), with access originating from home networks or devices over which the business may have little or no control?
Information security has long been a priority for IT, but in 451 Research's Voice of the Enterprise: Digital Pulse, Coronavirus Flash Survey October 2020, enterprises told us that the questions raised by the impact of the outbreak had moved it to the front of the line.
Figure 1: Which of the following technology objectives, if any, have become a greater priority for your organization due to the influence of the coronavirus outbreak? Please select all that apply:
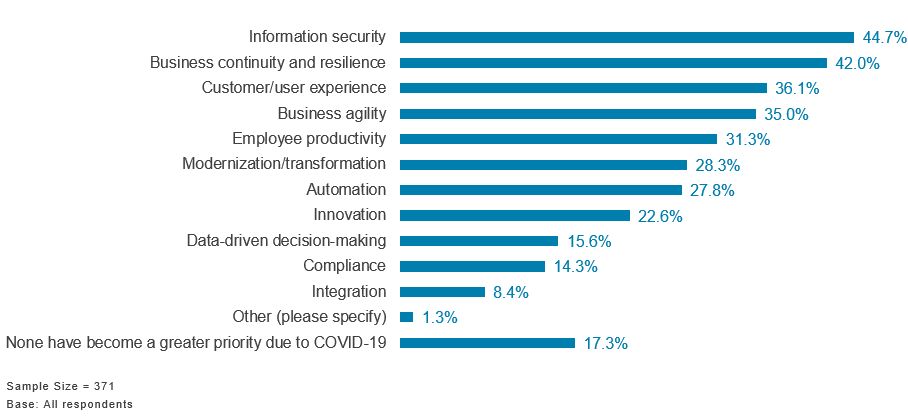
The heightened priority given to security coincides with rising interest in security technologies that can help answer these concerns. For example, when individuals seek access to a variety of target resources from home networks or other points of origin unknown to, or unmanaged by, the enterprise, they may need to invest in higher-confidence ways to validate that access. This, in turn, drives interest in technologies such as zero trust network access (ZTNA), and its continued expansion from authorization and network access toward getting a better handle on resource authorization and privilege management for target applications. Meanwhile, extending the connectivity, performance and availability that can scale along with the demand for ensuring policy-based security control from anywhere continues to spur interest in the secure access service edge (SASE) trend.
But if COVID-19 catalyzed the adoption of these techniques, it's at least in part because the need had been brewing well before meeting the demands of a pandemic forced IT's hand. The adoption of third-party IT services has been increasing for years, stressing security's ability to cope with the changes they bring. Legacy implementations of security measures often don't embrace the variety of modern IT – which, according to our VotE: Digital Pulse studies, will soon run the gamut of deployment models.
Figure 2: Which of the following best describes the primary environment used to operate your organization's workloads today? And which of the following best describes the primary environment in which your workloads will be operated two years from now?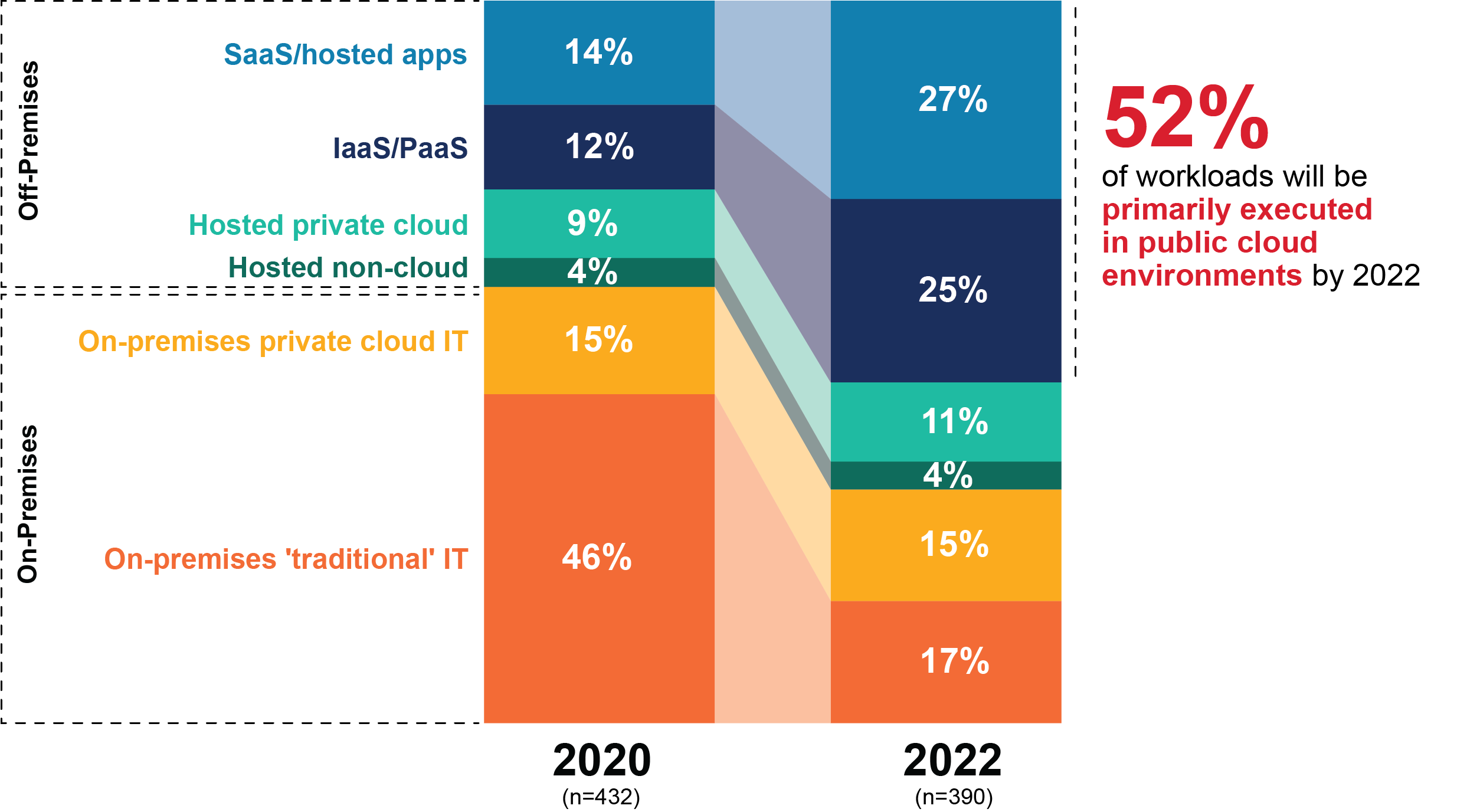
Increased reliance on all of these models means more than embracing new approaches to security architecture. It means increased complexity as well. Everything from the management of access and entitlements on an unprecedented scale to consistent governance for this variety of assets is in flux. Security telemetry along with the tactics of threat detection and response will have to look to a range of new sources and venues, which will force a rethink of the nature of security operations. Decreased dependence on the legacy enterprise network means increased dependence on endpoints and the security of target applications.
The sheer sprawl of the IT footprint beyond the boundaries of the traditional enterprise means that organizations will have to embrace new ways of assessing the comprehensive attack surface and dealing with a host of exposures. It's not just the growth in the variety of enterprise endpoints, which increasingly include operational technologies and enterprise IoT, where growth is expected to be substantial. According to 451 Research's Internet of Things Market Monitor data, the number of connected devices in the enterprise (not including consumer technologies) may grow over the next five years as much as 75% over the nearly eight billion estimated in 2019. From breach and attack simulation and continuous automated security testing and validation of the IT environment, to measuring third-party risk, gathering an asset inventory, or assessing the comprehensive attack surface, even when it extends beyond the enterprise network per se – these are all areas where we expect to see increased investment as enterprises scramble to broaden their focus to get a handle on the sheer extent of their exposure.
For years, the enterprise has focused on going deep – increased responsiveness to detailed insight into the nature of penetration and compromise. The pandemic is escalating the equally important demand to go wide, tackling the reality of IT sprawl and the changed nature of control that the expansive use of third-party resources and a far-flung edge demand. While inevitable, it once seemed likely that these changes would only unfold slowly over time – but the events of 2020 have already forced some significant shifts in investment.
In both our March and June Coronavirus Flash Surveys, infosec software and tools were among the top four categories where organizations of all sizes expected to increase spending because of COVID-19 – and as our practitioner interviews describe, the increased investment in remote work has to come from somewhere. ("Let's call it, 1,200 people that are working from home, and you're spending like $1,200 on a laptop, you're at $1.5m right there. You can't buy that and just keep paying for empty offices, electric, heating, cooling, parking.") Not surprisingly, nearly one-third of respondents to our October Flash Survey told us they expected to see a 32% reduction in office footprint, paralleling a 64% permanent increase in remote work.
Figure 3: Permanent Changes Made in Response to COVID-19
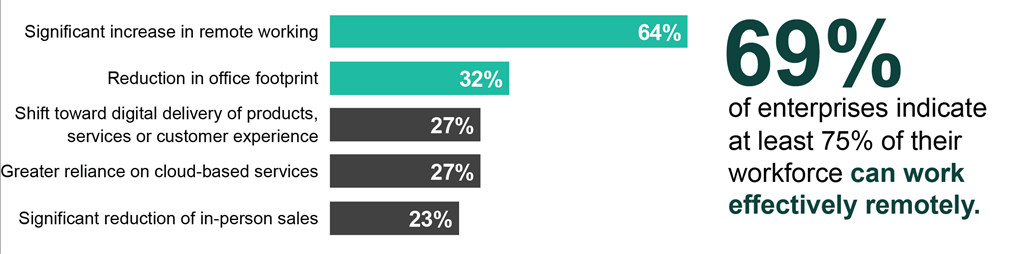
Given the heightened priority of securing business that emerges on the other side, security may ultimately be among the beneficiaries of spending shifts catalyzing investment in new and very much needed approaches to keeping the enterprise safe, no matter how widely distributed and shared its resources may be.
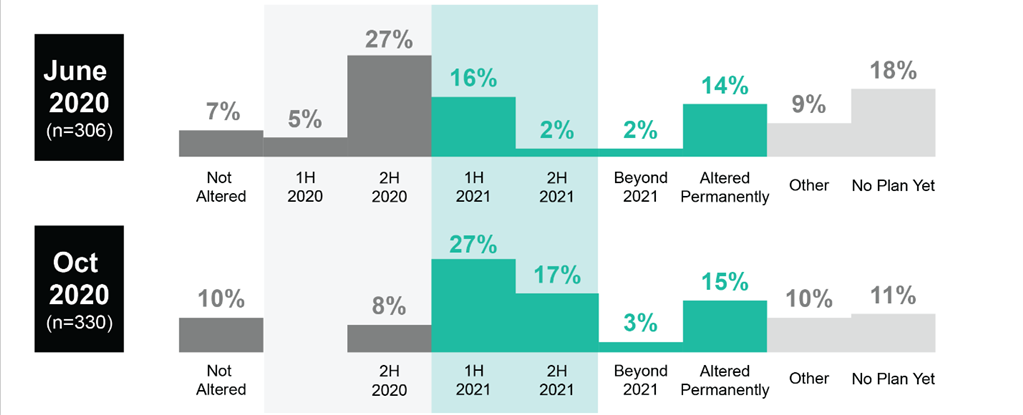
Adapting to these realities will not happen overnight. But then, neither will recovery from the changes wrought by the pandemic. In our Coronavirus Flash Survey from June, 27% of respondents expected operations under pandemic-altered conditions to end in the second half of 2020, with 16% anticipating this end in the first half of 2021. In our October 2020 survey, virtually those exact same percentages had shifted by six months: 27% expected an end to altered operating conditions in the first half of 2021, while 17% projected the end in the second half of 2021. Meanwhile, an almost identical percentage in both surveys (14% and 15%, respectively) anticipated conditions to be altered permanently. Combined, these responses represent the majority of respondents to each survey.
Figure 4: How long is your organization planning to have to operate under altered conditions (e.g., remote work, wearing PPE, social distancing, enhanced cleaning practices) as a result of the coronavirus outbreak?
Security must adapt to the changing nature of enterprise IT. Coronavirus may be catalyzing the investment necessary to do so. It will take time – the need for far-reaching change is substantial – but as businesses emerge from the 'new abnormal' to a future hopefully changed for the better, we would hope for the landscape of security to be changed for the better as well.



